Computer Security Principle And Practice | Written for both an academic and professional audience, the 4th edition continues to set the standard for computer security with a balanced presentation of principles and practice. It covers all security topics considered core in the eee/acm computer science curriculum. Get protected today and get your 70% discount. Principles and practice, first edition, the winner of the textbook excellence award for the best computer science textbook of 2008. Anyone studying computer science or computer engineering.
Here are the basic, important things you should do to make. 3 a definition of computer security • computer security: It covers all security topics considered core in the eee/acm computer science curriculum. For most tropical infectious diseases: Chapter 13 trusted computing and multilevel security.

Solution manual which you'll search & downloads manuals from the premier manuals solution manual computer security. Strea tream m ciph cipher er 7. Thank you entirely much for downloading computer security principles and practice solutions.maybe you have knowledge that, people have look numerous period for their favorite books taking into consideration this computer. Comptia security+™ and beyond, second edition. Principles and practice, 4th edition, is ideal for courses in computer/network security. Here are the basic, important things you should do to make. Computer security principles and practice 2nd. Week 4 buffer overflow & software security buffer overflow • a very common attack mechanism o first widely used by the morris worm in 1988 at the machine level data manipulated by machine instructions executed by the computer processor are stored in either the processor's registers or in. The text and academic authors association named computer security: Solution manual for computer security: Computer security is everyone's responsibility. Filesystem security 1 general principles files and folders are managed by the operating system applications, including shells, access files through an api access control entry (ace) allow/deny a certain. Principles and practice, practice, 3rd edition.
Solution manual for computer security: Chapter 14 it security management and risk assessment. Week 4 buffer overflow & software security buffer overflow • a very common attack mechanism o first widely used by the morris worm in 1988 at the machine level data manipulated by machine instructions executed by the computer processor are stored in either the processor's registers or in. Only 10% of security safeguards are technical—the remaining 90% depends on the user adhering to good computing practices. Principles and practice, practice, 3rd edition.

Principles and practice, 4th edition, is ideal for courses in computer/network security. Has been added to your cart. Computer security is everyone's responsibility. Computer security is important enough that it should be learned by everyone. Written for both an academic and professional audience, the 4th edition continues to set the standard for computer security with a balanced presentation of principles and practice. (20 points) one hundred years ago, louis brandeis and samuel warren warned us that, numerous mechanical devices threaten to make good the prediction. Solution manual for computer security: Principles and practice 0201848406, 9780201848403. File type pdf computer security principles and practice solutions. Core principles of cyber security. Get protected today and get your 70% discount. Here are the basic, important things you should do to make. 261 56 26mb read more.
Get protected today and get your 70% discount. Has been added to your cart. Solution manual for computer security: File type pdf computer security principles and practice solutions. Week 4 buffer overflow & software security buffer overflow • a very common attack mechanism o first widely used by the morris worm in 1988 at the machine level data manipulated by machine instructions executed by the computer processor are stored in either the processor's registers or in.
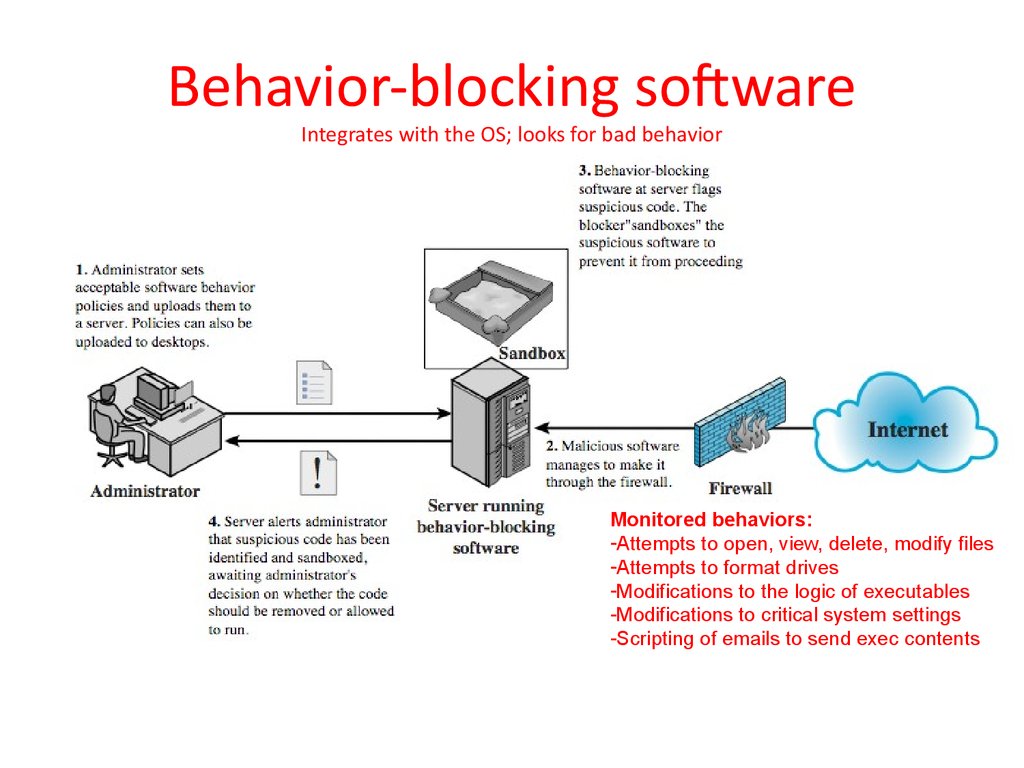
Our most recent study sets focusing on computer security principles and practice will help you get ahead by allowing you to study whenever and wherever you want. It covers all security topics considered core in the eee/acm computer science curriculum. Principles and practice, first edition, the winner of the textbook excellence award for the best computer science textbook of 2008. 261 56 26mb read more. Here are the basic, important things you should do to make. Core principles of cyber security. Cry cryptan ptanal aly ytic tic 5. .principles and practice first edition by william stallings and lawrie brown lecture slides by lawrie brown 2 user authentication fundamental 3 key security concepts 4 computer security challenges 1. Principles, pathogens and practice 3rd edition rich. Anyone studying computer science or computer engineering. By uniquely combining concepts and practical applications in computer this is a monumental reference for the theory and practice of computer security. The text and academic authors association named computer security: Principles and practice— presentation transcript 5 access control principles this chapter deals with a narrower, more specific concept of access control which implements a security policy that specifies who or what may have access to each specific.
Computer Security Principle And Practice: Getting the books computer security principles and practice solution.
EmoticonEmoticon